Azure Service Principle Authentication
I have recently been working within a client where all Azure/ Office 365 users must perform MFA on logon.
Ages ago I posted about using credential manager to automate Office 365 scripts: https://blog.oholics.net/using-credential-manager-to-authenticate-office-365-scripts/. This method will clearly not suffice where MFA is enforced, as there is no mechanism to allow MFA challenge and response.
Recently I have been looking into using Azure Service Principle objects to bypass MFA and to allow scripts, that need to connect to Azure or other services, to do so without input. Thus, I can then schedule scripted tasks to generate reports on Azure AD objects or AzureRM items.
Firstly I need to create some certificates, these will be used to authenticate, see here: https://blog.oholics.net/creating-simple-ssl-certificates-for-server-authentication-using-openssl/ for details on certificate creation.
Next, once we have the PFX certificate file, we can create the Azure App Registration, using PowerShell:
Then (optionally), if the script that you want to automate will be reading AzureRM objects, run the following script. Note that if the role assignment is to be constrained to a specific resource group, add the -ResourceGroupName switch to New-AzureRMRoleAssignment
Additionally, the RoleDefinitionName can be altered to suit.
Now we have the Service Principle in place, we can connect! But in the case of the Azure AD connection, I need to first allow the application to Read AAD:
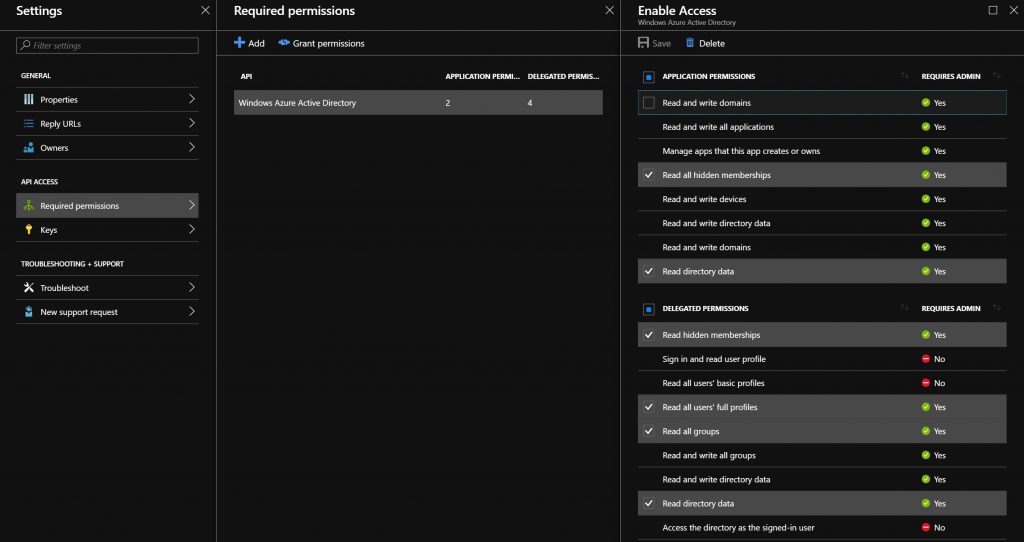
Go to the App Registrations blade in Azure AD, pick the application created earlier, then select settings. Select Required Permissions, add Azure AD and add the permissions shown in the following image:
Now lets connect using the certificate thumbprint:
By installing the certificate in the CurrentUser store, only that user can consume the certificate thumbprint for authentication using this method. Lovely.. 🙂
Why is this method secure?
- You can only access the application to sign in if you have installed the certificate on the machine that you want to run the script from.
- To install the certificate, you must know the password that was set on the private key during PFX creation.
- No AAD user object is created
- No plain text passwords need to be stored
To sign in using this method, you must know:
- The AAD Tenant GUID
- The Application GUID of the configured application
- The specific thumbprint of the certificate, used to make the connection
- The certificate and private key must be installed on the machine on which the connection attempt is being made.