Firewalla – Allowed IP Addresses for Ring Camera Devices
My initial setup of Ring Camera’s with my Firewalla was pretty lacklustre! They were isolated in a device group from all other networks, but had free outbound access to the internet. So, at first I got a few alerts for domains like ring.com and added these as allow rules. Everything was generally good, but I constantly got “unusual upload” alerts on the Firewalla for my Ring cameras, these were always Ireland based IP’s associated with Amazon. Each time I got an alert, I added it to the mute/ exclusion list, but this was burdensome!
Then as mentioned in my last post (https://blog.oholics.net/s3-amazonaws-com-dns-resolution-and-firewalla/), I started locking stuff down, including my Ring cameras, following the same process as I used for my PiHole. I googled “allowed IP addresses for Ring cameras” previously and got the gist that there is no easy way.
After the success I had with my previous use of Target Lists on the Firewalla , I looked to use the same approach for this issue. After locking down the device group, I noted that the target IP’s were nearly all West EU based IP’s for the AMAZON service, so needed to add some more arguments to my jq query – I needed the ranges for the AMAZON service in eu-west-1, eu-west-2 and eu-west-3. To do so, I used the test argument, as follows:
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r ‘.prefixes[] | select(.region|test(“^eu-west.”)) | select(.service==”AMAZON”) | .ip_prefix’
I added those ranges (574 in total) to 3 Firewalla Target Lists, each can hold a maximum of 200 CIDR ranges. 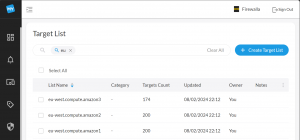
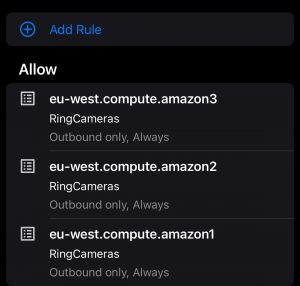
Then, I created rules to allow traffic from the Ring Camera’s group to the IP ranges in these Target Lists.
Then, after a few days I checked to see what was still being blocked and noted a handful of East US based Amazon IP’s, some were EC2 Service ranges, so I grabbed them with:
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r ‘.prefixes[] | select(.region|test(“^us-east.”)) | select(.service==”EC2″) | .ip_prefix’
Then I noted that some ranges were from the AMAZON service, so I grabbed them too:
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r ‘.prefixes[] | select(.region|test(“^us-east.”)) | select(.service==”AMAZON”) | .ip_prefix’
However, after I had the files containing the ranges, I realised that there was some duplication between the sets; some Amazon services share IP ranges, where the AMAZON service list covered EC2 as well. I added these ranges to new Target Lists using the Firewalla web interface.
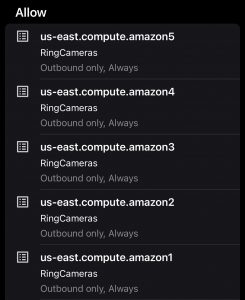
Back on my phone, I added rules to allow traffic to the IP ranges in these allow lists:
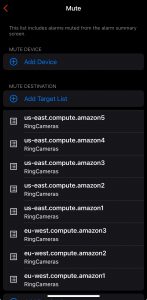
And then added those same Target Lists to the mute list for Abnormal Uploads, targeting the Ring Cameras group only.
Since I made these changes, I’m no longer seeing any blocked outbound traffic from my Ring cameras or any alerts relating to Abnormal Uploads 🙂