s3.amazonaws.com DNS Resolution and Firewalla
A few years ago I bought a Firewalla Gold device to help provide some additional protection to my home network, but more importantly to control what my kids had access to and when they had internet access.
My initial setup was fairly basic, but did the job. I’ve also been running PiHole and Unbound on a Raspberry Pi Zero 2, which has been very effective at black-holing advertising and other undesirable DNS traffic.
Over the Christmas/ new year holiday, I got hold of a Cisco switch which was capable of VLAN tagging, so set about having a bit of a tidy up/ isolation of devices/ networks.
I made the following changes:
- Created a VLAN for the PiHole, the Zero 2 is hardwired via an Amazon Firestick network adaptor.
- Created a device group on the Firewalla, which only contains that Zero 2.
- Allowed incoming port 53 connections from all internal networks/ VLANs to the Zero 2.
- Blocked all inbound and outbound traffic from the PiHole VLAN.
- Permitted port 53 outbound traffic (public) from the Zero 2.
Now the network is isolated, I updated gravity on the PiHole to see what is now blocked, then added allow rules for all desired traffic.
One allow rule added was for s3.amazonaws.com as two of the blocklists were hosted in S3 buckets. That is the back story, now onto the problem and my solution.
The problem: When Gravity ran on the PiHole, it always failed to get the two blocklists that were hosted on s3.amazonaws.com, even though I had an allow rule on the Firewalla for that domain.
Why: Amazon services are massive and widely distributed! Resolution of DNS will provide a different set of IP’s every time you try. The image below shows my Pihole on the left and the Firewalla console on the right: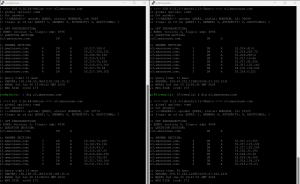
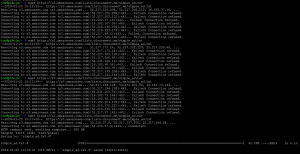 The Firewalla was supposed to learn the IP’s of the domain to honour the allow rule. However, after making all the changes requested in my support ticket with Firewalla, the issue remained. Note that some IP’s were trusted and (most) others were not, see:
The Firewalla was supposed to learn the IP’s of the domain to honour the allow rule. However, after making all the changes requested in my support ticket with Firewalla, the issue remained. Note that some IP’s were trusted and (most) others were not, see:
So the fix… Initially I figured that I would just pick a “trusted” IP and add it to the PiHole local DNS, that worked but wasn’t very resilient! So, then I looked at how I could tell Firewalla to trust all IP’s associated to the S2 namespace.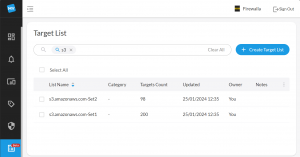
How to do that? Amazon provide a good article on identifying the IP addresses used for their services here: https://repost.aws/knowledge-center/s3-find-ip-address-ranges. Using this method, I obtained 298 IP ranges in CIDR format. I then added these to Firewalla Target Lists, via the browser interface.
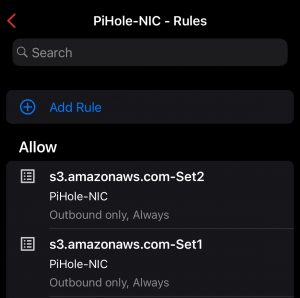
Then, back on my phone, added an allow rule for each set of Target Lists:
Now I can freely get the block lists from any s3.amazonaws.com IP address 😉
Sure I have added a lot of “trusted IP’s”, a lot more than planned, but these rules apply only to that device and are outbound only.