SharePoint Foundation 2013 – Setup is Unable to Proceed due to following error, requires .Net Framework 4.5
I have been setting up a MIM PAM lab at home. Following the guide here: https://technet.microsoft.com/en-us/library/mt488766.aspx
I’m installing onto Server 2012 R2, with SharePoint Foundation 2013 SP1
After installing the SharePoint Foundation 2013 Prerequisites, using the Service Pack 1 release, all installs just fine. Then I run the setup.exe, very quickly I’m prompted with the message “Setup is Unable to Proceed due to following error, requires .Net Framework 4.5“. The prerequisite installation log (C:\Users\<MyUserAccount>\AppData\Local\Temp\) shows:
2016-01-29 22:39:36 – Check whether the following prerequisite is installed:
2016-01-29 22:39:36 – Microsoft .NET Framework 4.5
2016-01-29 22:39:36 – Reading the following DWORD value/name…
2016-01-29 22:39:36 – Install
2016-01-29 22:39:36 – from the following registry location…
2016-01-29 22:39:36 – SOFTWARE\Microsoft\Net Framework Setup\NDP\V4\full
2016-01-29 22:39:36 – The value is (1)
2016-01-29 22:39:36 – Reading the following string value/name…
2016-01-29 22:39:36 – Version
2016-01-29 22:39:36 – from the following registry location…
2016-01-29 22:39:36 – SOFTWARE\Microsoft\Net Framework Setup\NDP\V4\full
2016-01-29 22:39:36 – The value is…
2016-01-29 22:39:36 – 4.6.01055
2016-01-29 22:39:36 – A post release .NET 4.5 is installed
However, the SharePoint Foundation installation log shows:
2016/01/30 19:27:00:389::[3788] Catalyst .Net version check failed. Setup requires .Net Framework version 4.5.50501 to install this product
4.6.01055 is installed but the installer wants the older version – 4.5.50501.
So, after a bit of googling, I find this: https://social.technet.microsoft.com/Forums/sharepoint/en-US/bbed58e1-4a80-4dde-91fd-c6fc95bf85ac/sharepoint-2013-installation-with-net-framework-4550501-and-4550709?forum=sharepointadmin
In that post, Rick just sets all of the registry entries. However, the one that seems to be the ‘looked up’ value (at least based on my testing today), which is contrary to the prerequisite log, is HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v4\Client.
Detailed method:
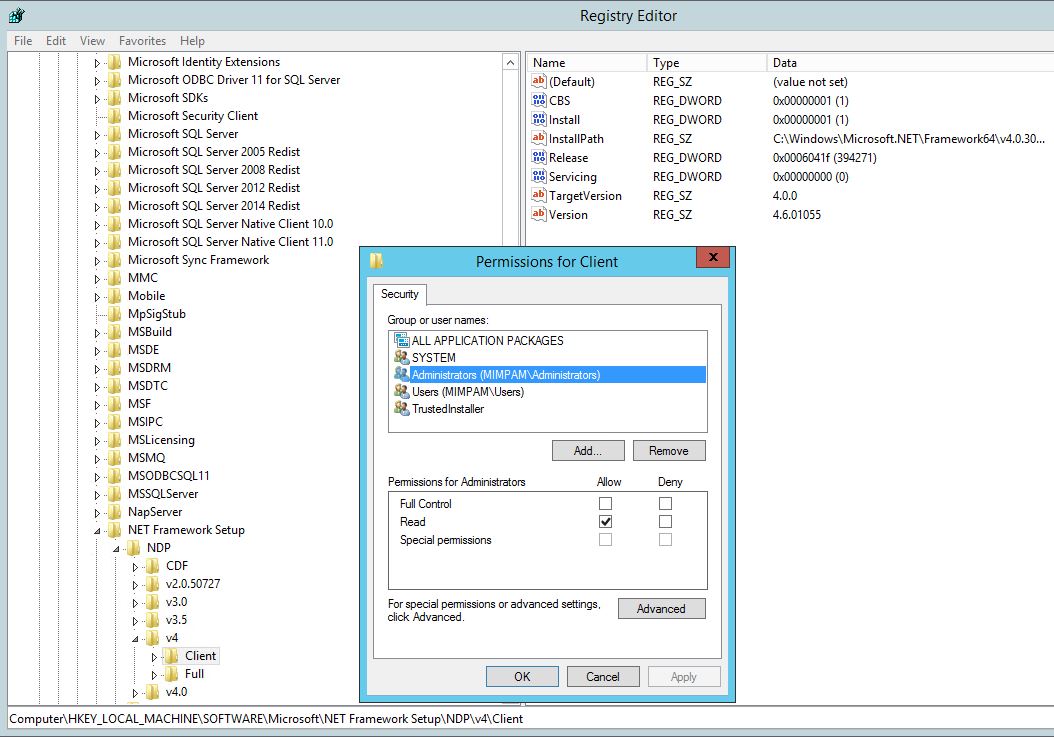
Right click the Client key, choose Permissions…
Note that the Administrators group has Read access by default.
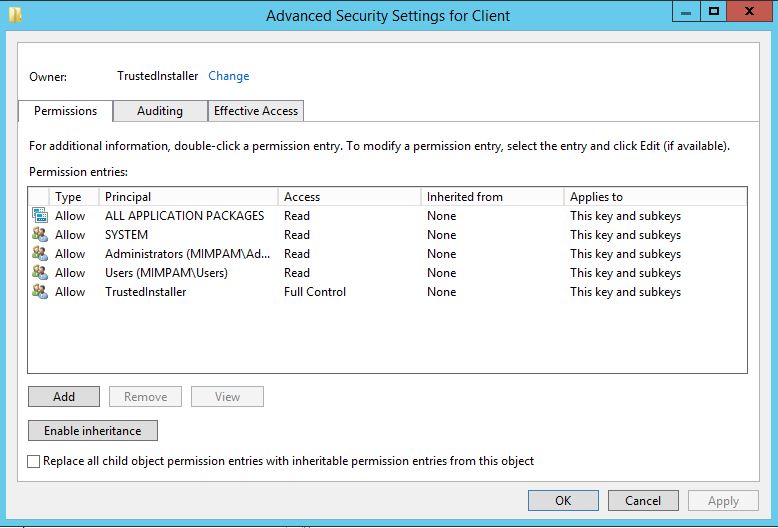
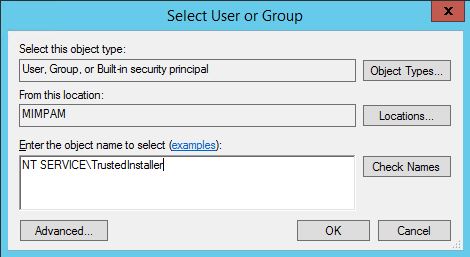
Click Advanced, note at the top of the window, the owner is shown as TrustedInstaller:
Click the Change link beside the owner label.
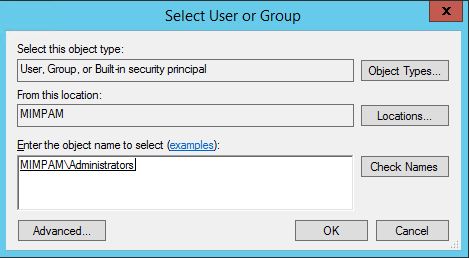
Change the scope (“From this location”), to the local machine, choose <localmachine>\administrators group:
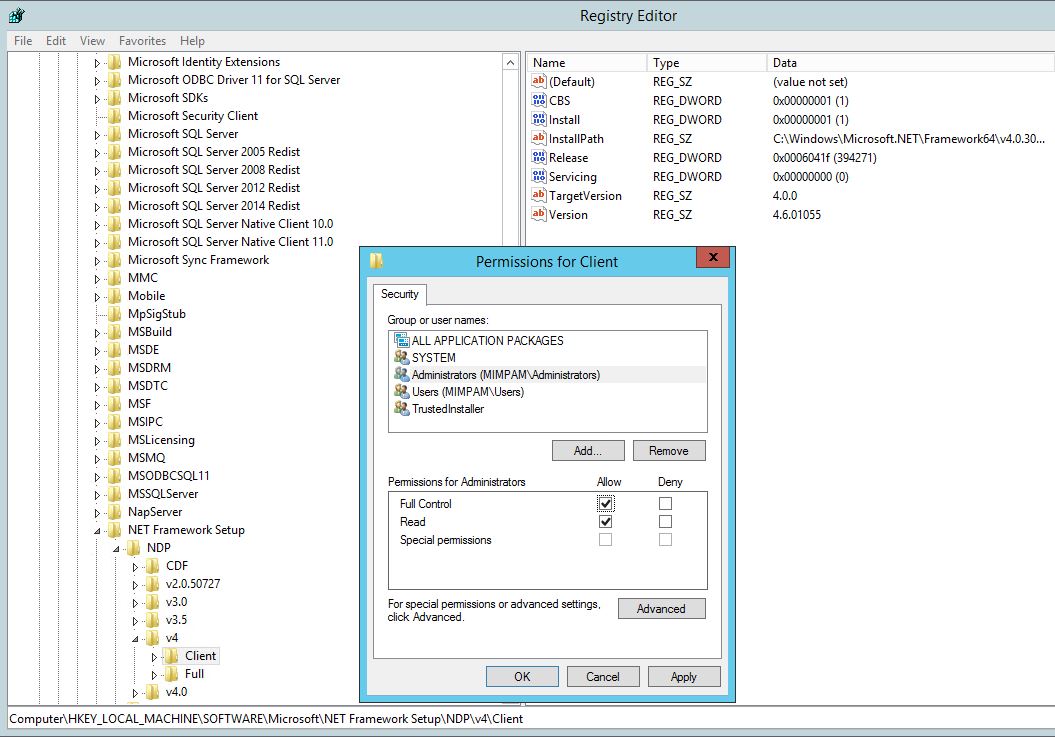
Click OK, then OK again until we are back at the initial Permissions window, tick Full Control for the Administrators group:
OK, then go set the Version number to 4.5.50501
Install SharePoint Foundation 2013.
Once complete, put things back to how they were before – of course this is optional….. just depends on how lazy you feel and whether you want to be caught out by the fact that you changed this sometime in the future, then can’t figure out why something else doesn’t work. Making the change back is so straightforward and quick, I believe that it is worth doing 🙂
After installation, flip version back to 4.6.01055. Then, right click the Client key, remove full control from the Administrators group, apply. Then, click Advanced, go and change the Owner again – as before but using NT SERVICE\TrustedInstaller as the owner:
Click OK, until you are back to Square 1. Easy!